好有勇氣的工程師,直接拿 cookie 裡的 username 組合起來執行外部指令,就跟SQL Injection 一樣危險。這個WD MyCload的漏洞,補一下就可填起來了,對 username 加入更多的檢查就OK了。
好有勇氣的工程師,直接拿 cookie 裡的 username 組合起來執行外部指令,就跟SQL Injection 一樣危險。這個WD MyCload的漏洞,補一下就可填起來了,對 username 加入更多的檢查就OK了。
資料來源:
Hacking the Western Digital MyCloud NAS
https://blog.exploitee.rs/2017/hacking_wd_mycloud/
直接 Demo WD 的 MyCloud 有那些漏洞沒寫好,應該有很多是軟體工程師的疏失,在寫網路相關的程式應該要去注意。
Western Digital MyCloud Multiple Remote Root Exploits
https://www.youtube.com/watch?v=aKu_yWrIIFI
Command Injection Bugs
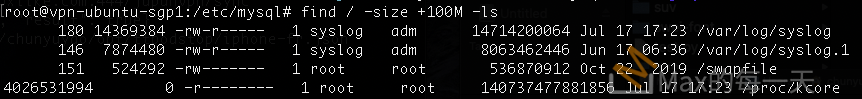
A majority of the functionality of the WDCloud web interface is actually handled by CGI scripts on the device. Most of the binaries use the same pattern, they obtain post/get/cookie values from the request, and then use the values within PHP calls to execute shell commands. In most cases, these commands will use the user supplied data with little or no sanitization. For example, consider the following code from the device.
php/users.php
15 $username = $_COOKIE['username'];
16 exec("wto -n \"$username\" -g", $ret);
The code above assigns a value from the COOKIE superglobal variable, which contains array indexes for cookies submitted from the request, to the local variable “$username”. This value is then immediately used in a PHP “exec()” call as an argument to the local “wto” binary. Since there is no sanitization, using a username value like