相同的操作流程, 在ubuntu server 上是可以登入的, 但無法在 Rocky linux 的 ssh 上登入, 錯誤訊息:
No supported authentication methods available
解法:
- Login with public key not working
https://forums.rockylinux.org/t/login-with-public-key-not-working/7939 - Using system-wide cryptographic policies
https://access.redhat.com/documentation/zh-tw/red_hat_enterprise_linux/8/html/security_hardening/using-the-system-wide-cryptographic-policies_security-hardening - Configure system-wide cryptographic policies on RHEL/CentOS/Rocky
https://computingforgeeks.com/configure-system-wide-cryptographic-policies/
執行指令:
grep ssh-rsa /etc/crypto-policies/back-ends/opensshserver.config | cut -d' ' -f1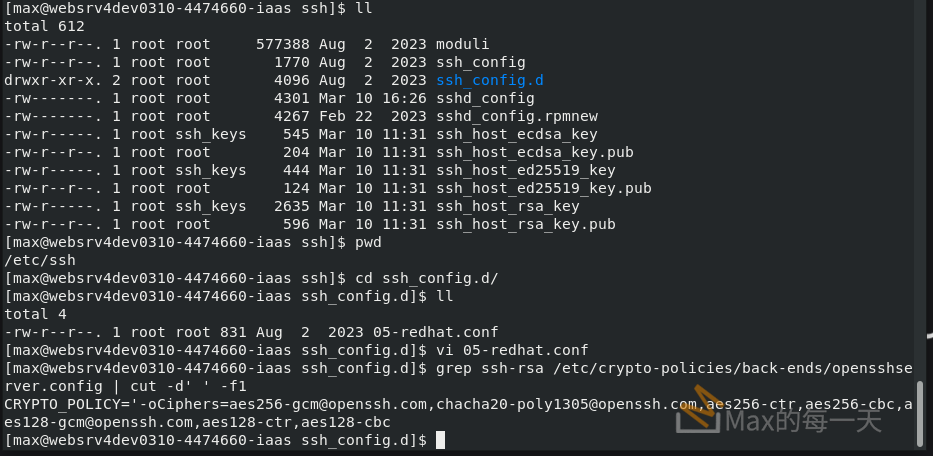
可以看到, 加密的規則, 不含 ed25519 或 ed25519, 居然都只有 aes.
RHEL 8 contains the following predefined policies:
- DEFAULT
The default system-wide cryptographic policy level offers secure settings for current threat models. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 2048 bits long. - LEGACY
Ensures maximum compatibility with Red Hat Enterprise Linux 5 and earlier; it is less secure due to an increased attack surface. In addition to the DEFAULT level algorithms and protocols, it includes support for the TLS 1.0 and 1.1 protocols. The algorithms DSA, 3DES, and RC4 are allowed, while RSA keys and Diffie-Hellman parameters are accepted if they are at least 1023 bits long. - FUTURE
A stricter forward-looking security level intended for testing a possible future policy. This policy does not allow the use of SHA-1 in signature algorithms. It allows the TLS 1.2 and 1.3 protocols, as well as the IKEv2 and SSH2 protocols. The RSA keys and Diffie-Hellman parameters are accepted if they are at least 3072 bits long. If your system communicates on the public internet, you might face interoperability problems. - FIPS
Conforms with the FIPS 140 requirements. The fips-mode-setup tool, which switches the RHEL system into FIPS mode, uses this policy internally. Switching to the FIPS policy does not guarantee compliance with the FIPS 140 standard. You also must re-generate all cryptographic keys after you set the system to FIPS mode. This is not possible in many scenarios.
安裝套件:
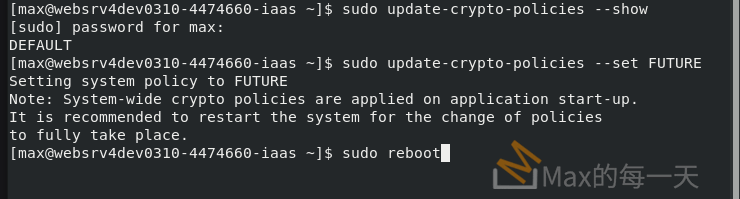
sudo yum -y install crypto-policies-scripts檢查目前 policies:
sudo update-crypto-policies --show切換system-wide cryptographic 為 LEGACY:
sudo update-crypto-policies --set LEGACYPS: 設成 FUTURE , 會造成remote desktop 無法登入。
執行畫面:
ssh 操作流程, 請參考:
How To Configure SSH Key-Based Authentication on a Linux Server
https://www.digitalocean.com/community/tutorials/how-to-configure-ssh-key-based-authentication-on-a-linux-server
在 sshd_config 上寫著:
# This system is following system-wide crypto policy. The changes to
# crypto properties (Ciphers, MACs, ...) will not have any effect here.
# They will be overridden by command-line options passed to the server
# on command line.
# Please, check manual pages for update-crypto-policies(8) and sshd_config(5).
意思是, sshd 是套用 system-wide crypto policy
Ubuntu 上 service 的設定:
[Unit]
Description=OpenBSD Secure Shell server
Documentation=man:sshd(8) man:sshd_config(5)
After=network.target auditd.service
ConditionPathExists=!/etc/ssh/sshd_not_to_be_run
[Service]
EnvironmentFile=-/etc/default/ssh
ExecStartPre=/usr/sbin/sshd -t
ExecStart=/usr/sbin/sshd -D $SSHD_OPTS
ExecReload=/usr/sbin/sshd -t
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=on-failure
RestartPreventExitStatus=255
Type=notify
RuntimeDirectory=sshd
RuntimeDirectoryMode=0755
[Install]
WantedBy=multi-user.target
Alias=sshd.service
Rocky Linux, /usr/lib/systemd/system/sshd.service
[Unit]
Description=OpenSSH server daemon
Documentation=man:sshd(8) man:sshd_config(5)
After=network.target sshd-keygen.target
Wants=sshd-keygen.target
[Service]
Type=notify
EnvironmentFile=-/etc/crypto-policies/back-ends/opensshserver.config
EnvironmentFile=-/etc/sysconfig/sshd
ExecStart=/usr/sbin/sshd -D $OPTIONS $CRYPTO_POLICY
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=on-failure
RestartSec=42s
[Install]
WantedBy=multi-user.target
$OPTIONS $CRYPTO_POLICY 的值, 是什麼?
建立新的虛擬主機, systemctl status sshd.service 取得的狀態如下:
/usr/sbin/sshd -D [email protected],[email protected],aes256-ctr,aes256-cbc,[email protected],aes128-ctr,aes128-cbc [email protected],hm>
如困是key 會失敗的主機: systemctl status sshd.service
/usr/sbin/sshd -D [email protected],chacha20-p>
/etc/crypto-policies/back-ends/opensshserver.config
正常主機:
CRYPTO_POLICY='[email protected],[email protected],aes256-ctr,aes256-cbc,[email protected],aes128-ctr,aes128-cbc [email protected],[email protected],[email protected],[email protected],hmac-sha2-256,hmac-sha1,[email protected],hmac-sha2-512 -oGSSAPIKexAlgorithms=gss-curve25519-sha256-,gss-nistp256-sha256-,gss-group14-sha256-,gss-group16-sha512-,gss-gex-sha1-,gss-group14-sha1- -oKexAlgorithms=curve25519-sha256,[email protected],ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1 -oHostKeyAlgorithms=ecdsa-sha2-nistp256,[email protected],ecdsa-sha2-nistp384,[email protected],ecdsa-sha2-nistp521,[email protected],ssh-ed25519,[email protected],rsa-sha2-256,[email protected],rsa-sha2-512,[email protected],ssh-rsa,[email protected] -oPubkeyAcceptedKeyTypes=ecdsa-sha2-nistp256,[email protected],ecdsa-sha2-nistp384,[email protected],ecdsa-sha2-nistp521,[email protected],ssh-ed25519,[email protected],rsa-sha2-256,[email protected],rsa-sha2-512,[email protected],ssh-rsa,[email protected] -oCASignatureAlgorithms=ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519,rsa-sha2-256,rsa-sha2-512,ssh-rsa'有問題主機:
CRYPTO_POLICY='[email protected],[email protected],aes256-ctr,aes256-cbc,[email protected],aes128-ctr,aes128-cbc,3des-cbc [email protected],[email protected],[email protected],[email protected],hmac-sha2-256,hmac-sha1,[email protected],hmac-sha2-512 -oGSSAPIKexAlgorithms=gss-curve25519-sha256-,gss-nistp256-sha256-,gss-group14-sha256-,gss-group16-sha512-,gss-gex-sha1-,gss-group14-sha1- -oKexAlgorithms=curve25519-sha256,[email protected],ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1 -oHostKeyAlgorithms=ecdsa-sha2-nistp256,[email protected],ecdsa-sha2-nistp384,[email protected],ecdsa-sha2-nistp521,[email protected],ssh-ed25519,[email protected],rsa-sha2-256,[email protected],rsa-sha2-512,[email protected],ssh-rsa,[email protected],ssh-dss,[email protected] -oPubkeyAcceptedKeyTypes=ecdsa-sha2-nistp256,[email protected],ecdsa-sha2-nistp384,[email protected],ecdsa-sha2-nistp521,[email protected],ssh-ed25519,[email protected],rsa-sha2-256,[email protected],rsa-sha2-512,[email protected],ssh-rsa,[email protected],ssh-dss,[email protected] -oCASignatureAlgorithms=ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519,rsa-sha2-256,rsa-sha2-512,ssh-rsa,ssh-dss'試了很久, 還是登不進去, 不確定是不是環境的某一個神奇的設定值設定到, 造成無法登入。但是有問題的主機使用帳/密是可以登。
把虛擬主機刷成全新的,又可以使用 key 登入。而且, 預設的 policies 是: DEFAULT。神奇的是, 一改 port 這個新的主機上的 sshd 就會失敗。
把全新,可以用key 登入主機可以複製出來的參數, zip 起來後, 拿到有問題的主機上, unzip, 並重啟服務, 結果還是無法…, 只好找時間在這個新的可以登入的主機上, 重新安裝開發環境。
神奇的是, 在新創出來的虛擬主機上, 系統預設的管理員一般權限帳號是可以用key 登入, 自己手動創的帳號, 雖然卻不能登入, 比較這2個帳號的 env , export 都長一樣, 連 ~/.profile , ~/.bash_profile 都一樣…。
change port
修改port 在其他 linux 很簡單, 但在 rocky linux 很麻煩, 修改後會無法啟動服務,
If you want to allow /usr/sbin/sshd to bind to network port 12345
Then you need to modify the port type.
Do
# semanage port -a -t PORT_TYPE -p tcp 12345
where PORT_TYPE is one of the following: ssh_port_t, vnc_port_t, xserver_port_t.
***** Plugin catchall_boolean (7.83 confidence) suggests ******************
If you want to allow nis to enabled
Then you must tell SELinux about this by enabling the 'nis_enabled' boolean.
Do
setsebool -P nis_enabled 1
***** Plugin catchall (1.41 confidence) suggests **************************
If you believe that sshd should be allowed name_bind access on the port 19790 tcp_socket by default.
Then you should report this as a bug.
You can generate a local policy module to allow this access.
Do
allow this access for now by executing:
# ausearch -c 'sshd' --raw | audit2allow -M my-sshd
# semodule -X 300 -i my-sshd.pp
Ex:
sudo semanage port -a -t ssh_port_t -p tcp 12345
sudo setsebool -P nis_enabled 1加了上面二行, 居然就可以用了, 現在自己新創的帳號, 也可以用key 登入。
預設, 是沒有防火牆, 在執行上面二行指令後, 防火牆就會被開啟。
需要手動加入你想開啟的port:
sudo firewall-cmd --permanent --add-port=12345/tcp
sudo firewall-cmd --reload為避免遇到的情況太複雜, 建議你的Rocky Linux 在一開始可以先升級主機的第三方套件:
sudo dnf update
最好可以安裝 net-tools , 以便使用 netstat 指令:
sudo dnf install net-tools最後, reboot. 可以減少遇到鬼打牆的機率。
重新開了一台新的Server, 結果新創的帳號, 還是無法ssh 用key 登入. @_@; 太神奇了.
附註: 改 port 在防火牆要先開好規則, 不然會連不進去, 預設 Rocky Linux 8.9 一開始沒開防火牆, 只安裝 GUI (指令: sudo yum groupinstall "Server with GUI") , 重開機後, 就防火牆就被啟用了.
相關討論
Ssh key login not working with root
https://forums.rockylinux.org/t/ssh-key-login-not-working-with-root/7416
How to Fix SSH Failed Permission Denied (publickey,gssapi-keyex,gssapi-with-mic)
https://phoenixnap.com/kb/ssh-permission-denied-publickey
Unable to remove cipher suites from ssh
https://forums.rockylinux.org/t/unable-to-remove-cipher-suites-from-ssh/5226/14
Cannot start sshd
https://forums.rockylinux.org/t/cannot-start-sshd/7727
使用第三方SSH客户端远程连接Linux实例时,提示“No supported authentication methods available (server sent: publickey,gssapi-keyex,gssapi-with-mic)”错误怎么办?
https://help.aliyun.com/zh/ecs/support/the-disconnected-no-supported-authentication-methods-available-error-occurs-when-you-log-on-to-a-linux-instance-by-ssh